Patent application title: SUPPORTING SPECULATIVE MODIFICATION IN A DATA CACHE
Inventors:
Guillermo Rozas (Los Gatos, CA, US)
Guillermo Rozas (Los Gatos, CA, US)
Alexander Klaiber (Mountain View, CA, US)
Alexander Klaiber (Mountain View, CA, US)
David Dunn (Sammamish, WA, US)
David Dunn (Sammamish, WA, US)
Paul Serris (Sunnyvale, CA, US)
Lacky Shah (Fremont, CA, US)
IPC8 Class: AG06F1208FI
USPC Class:
711144
Class name: Caching coherency cache status data bit
Publication date: 2015-05-28
Patent application number: 20150149733
Abstract:
Method and system for supporting speculative modification in a data cache
are provided and described. In one embodiment, a speculative cache buffer
includes a plurality of cache lines and a plurality of state indicators.
At least one of the cache lines is operable to receive an evicted cache
line from a cache. The at least one of the cache lines is operable to
return the evicted cache line to the cache if the cache requests the
evicted cache line. Further, the plurality of state indicators is
operable to indicate a state of a corresponding cache line of the cache
lines.Claims:
1. A speculative cache buffer comprising: a plurality of cache lines,
wherein at least one of the cache lines is operable to receive an evicted
cache line from a cache, wherein the at least one of the cache lines is
operable to return the evicted cache line to the cache if the cache
requests the evicted cache line, and wherein if data is stored in the
cache lines, the data has been received from the cache; and a plurality
of state indicators operable to indicate a state of a corresponding cache
line of the cache lines.
2. The speculative cache buffer of claim 1, wherein the evicted cache line includes speculatively modified data.
3. The speculative cache buffer of claim 1, wherein the evicted cache line includes dirty data.
4. The speculative cache buffer of claim 1, wherein the plurality of state indicators include an invalid state, a dirty state, and a speculative state.
5. The speculative cache buffer of claim 4, wherein the plurality of state indicators include a commit-kill state.
6. The speculative cache buffer of claim 5, wherein if the state indicator of a cache line is the commit-kill state, the state indicator is changed to the invalid state in response to a commit operation.
7. The speculative cache buffer of claim 5, wherein if the state indicator of a cache line is the commit-kill state, the state indicator is changed to the dirty state in response to a rollback operation.
8. The speculative cache buffer of claim 1, wherein if the state indicator of a cache line is a dirty state, the cache line is drained to a memory.
9. The speculative cache buffer of claim 8, wherein the state indicator is changed to an invalid state.
10. A method comprising: speculatively modifying a cache line of a cache; evicting the cache line from the cache to a speculative cache buffer, wherein if data is stored in cache lines of the speculative cache buffer, the data has been received from the cache; and retrieving the cache line from the speculative cache buffer to the cache.
11. The method of claim 10, wherein said evicting comprises: setting a state indicator of the cache line in the speculative cache buffer to a speculative state.
12. The method of claim 11, wherein in response to a rollback operation, setting the state indicator of the cache line in the speculative cache buffer to an invalid state.
13. The method of claim 11, wherein in response to a commit operation, setting the state indicator of the cache line in the speculative cache buffer to a dirty state.
14. The method of claim 10, wherein said retrieving comprises: setting a state indicator of the cache line in the speculative cache buffer to an invalid state.
15. The method of claim 10, further comprising: modifying a second cache line of the cache; evicting the second cache line from the cache to the speculative cache buffer; setting a state indicator of the second cache line in the speculative cache buffer to a commit-kill state; in response to a rollback operation, setting the state indicator of the second cache line in the speculative cache buffer to a dirty state; and in response to a commit operation, setting the state indicator of the second cache line in the speculative cache buffer to an invalid state.
16. A method comprising: evicting a cache line from a cache to a speculative cache buffer, wherein the cache line includes dirty data; if said evicting is initiated by a speculative store operation to the cache line, setting a state indicator of the cache line in the speculative cache buffer to a first state; and if said evicting is initiated by a non-speculative store operation to the cache line, setting the state indicator of the cache line in the speculative cache buffer to a second state.
17. The method of claim 16, wherein the first state is a commit-kill state.
18. The method of claim 17, wherein in response to a rollback operation, setting the state indicator of the cache line in the speculative cache buffer to a dirty state.
19. The method of claim 17, wherein in response to a commit operation, setting the state indicator of the cache line in the speculative cache buffer to an invalid state.
20. The method of claim 16, wherein the second state is a dirty state.
Description:
CROSS-REFERENCE TO RELATED APPLICATIONS
[0001] This application is a Continuation of and claims priority to U.S. patent application Ser. No. 11/807,629, filed on May 29, 2007, which is a Continuation of and claims priority to U.S. patent application Ser. No. 10/662,028, filed on Jul. 16, 2003, which are hereby incorporated by reference in their entirety.
FIELD
[0002] Embodiments generally relate to data caches. More particularly, embodiments relate to the field of supporting speculative modification in a data cache.
BACKGROUND
[0003] A data cache interacts with a processor to increase system performance. However, if the processor is speculatively executing instructions, a traditional data cache is unable to properly deal with speculative modifications.
SUMMARY
[0004] Method and system for supporting speculative modification in a data cache are provided and described.
BRIEF DESCRIPTION OF THE DRAWINGS
[0005] The accompanying drawings, which are incorporated in and form a part of this specification, illustrate embodiments, together with the description, serve to explain the principles of the disclosure.
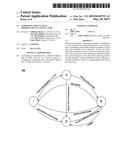
[0006] FIG. 1 illustrates a system in accordance with a first embodiment.
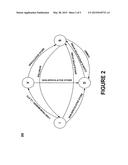
[0007] FIG. 2 illustrates a state diagram of a data cache in accordance with a first embodiment.
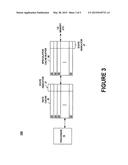
[0008] FIG. 3 illustrates a system in accordance with a second embodiment.
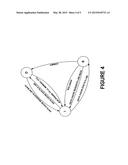
[0009] FIG. 4 illustrates a first state diagram of a speculative cache buffer in accordance with a second embodiment.
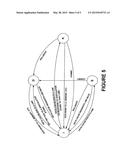
[0010] FIG. 5 illustrates a second state diagram of a speculative cache buffer in accordance with a second embodiment.
DETAILED DESCRIPTION
[0011] Reference will now be made in detail to embodiments, examples of which are illustrated in the accompanying drawings. While the disclosure will be described in conjunction with these embodiments, it will be understood that they are not intended to limit the disclosure to these embodiments. On the contrary, the disclosure is intended to cover alternatives, modifications and equivalents, which may be included within the spirit and scope of the disclosure as defined by the appended claims. Furthermore, in the following detailed description, numerous specific details are set forth in order to provide a thorough understanding. However, it will be recognized by one of ordinary skill in the art that embodiments may be practiced without these specific details.
[0012] FIG. 1 illustrates a system 100 in accordance with a first embodiment. As illustrated in FIG. 1, the system 100 includes a processor 10 and a data cache 20.
[0013] The processor 10 is able to speculatively execute instructions. If the processor 10 speculatively executes instructions to a particular instruction boundary without generating errors, the speculative store operations to the data cache 20 can be made permanent with a commit operation. However, if errors occur before reaching the particular instruction boundary, the speculative store operations to the data cache 20 have to be undone with a rollback operation.
[0014] The data cache 20 includes a plurality of cache lines 25. Each cache line includes a state indicator 27 for indicating any one of a plurality of states. The plurality of states include an invalid state, a valid state, a dirty state, and a speculative state. The invalid state indicates that the respective cache line is not being used. The valid state indicates that the respective cache line has clean data. The dirty state indicates that the respective cache line has dirty data (or the most recent data compared to other memory components such as L2 data cache, main memory, etc.). The speculative state enables keeping track of speculative modification to data in said respective cache line. The speculative state enables a speculative modification to the data in the respective cache line to be made permanent in response to a commit operation. Moreover, the speculative state enables the speculative modification to the data in the respective cache line to be undone in response to a rollback operation. Cache lines having the speculative state cannot be drained to other memory components such as L2 data cache, main memory, etc.
[0015] FIG. 2 illustrates a state diagram of a data cache in accordance with a first embodiment. As described above, a cache line can have an invalid state I, a valid state V, a dirty state D, or a speculative state S. (For clarity, state transitions from V, D, and S states to the I state, corresponding to the traditional operation of the data cache evicting a cache line, have been omitted in the figure.)
[0016] Invalid State I
[0017] Assuming the cache line is in the invalid state I, there are several possibilities for this cache line. If a non-speculative store is performed by the processor 10 (FIG. 1), the cache line moves to the dirty state D. If data is loaded from memory components such as L2 data cache, main memory, etc., the cache line moves to the valid state V, where the data is clean (has same version as the memory components such as L2 data cache, main memory, etc.). If a speculative store is performed by the processor 10 (FIG. 1), the cache line moves to the speculative state S.
[0018] Valid State V
[0019] Assuming the cache line is in the valid state V, there are several possibilities for this cache line. If a non-speculative store is performed by the processor 10 (FIG. 1), the cache line moves to the dirty state D. If a speculative store is performed by the processor 10 (FIG. 1), the cache line moves to the speculative state S.
[0020] Dirty State D
[0021] Assuming the cache line is in the dirty state D, there are several possibilities for this cache line. If a speculative store is performed by the processor 10 (FIG. 1) to this cache line, the cache line is first written back to a memory component such as L2 data cache, main memory, etc., thus preserving the cache line data as of before the speculative modification. Then, the speculative store is performed, moving the cache line to the speculative state S.
[0022] Speculative State S
[0023] Assuming the cache line is in the speculative state S, there are several possibilities for this cache line. If a commit operation is performed, the cache line moves to the dirty state D. If a rollback operation is performed, the cache line moves to the invalid state I.
[0024] FIG. 3 illustrates a system 300 in accordance with a second embodiment. The system 300 includes a processor 10, a data cache 20, and a speculative cache buffer 50. The discussion with respect to the processor 10 and the data cache 20 is equally applicable to FIG. 3.
[0025] The speculative cache buffer 50 receives cache lines which have the speculative state S and are evicted or drained from the data cache 20. Hence, the data cache 20 can send cache lines having the speculative state to the speculative cache buffer 50 and retrieve them when necessary.
[0026] Moreover, the speculative cache buffer 50 has a plurality of cache lines 55. Each cache line 55 includes a state indicator 57 for indicating any one of a plurality of states. The plurality of states includes an invalid state, a dirty state, and a speculative state. In one embodiment, the speculative cache buffer 50 is fully associative.
[0027] The data cache 20 can drain cache lines that are in the dirty state D or the speculative state S to the speculative cache buffer 50. Moreover, the speculative cache buffer 50 can drain cache lines that are in the dirty state D to a memory component such as L2 data cache, main memory, etc.
[0028] FIG. 4 illustrates a first state diagram of a speculative cache buffer in accordance with a second embodiment. As described above, a cache line can have an invalid state I, a dirty state D, or a speculative state S.
[0029] Invalid State I
[0030] Assuming the cache line is in the invalid state I, there are several possibilities for this cache line. If the data cache 20 evicts a cache line having the dirty state D, the cache line moves to the dirty state D. If the data cache 20 evicts a cache line having the speculative state S, the cache line moves to the speculative state S.
[0031] Dirty State D
[0032] Assuming the cache line is in the dirty state D, there are several possibilities for this cache line. If the speculative cache buffer 50 drains the cache line having the dirty state D to a memory component such as L2 data cache, main memory, etc., the cache line moves to the invalid state I. In case the data cache requests the cache line back, it moves to the invalid state I in the speculative cache buffer.
[0033] Speculative State S
[0034] Assuming the cache line is in the speculative state S, there are several possibilities for this cache line. If a commit operation is performed, the cache line moves to the dirty state D. If a rollback operation is performed, the cache line moves to the invalid state I. In case the data cache requests the cache line back, it moves to the invalid state I in the speculative cache buffer.
[0035] It is possible that multiple versions of a cache line in the dirty state may exist in the speculative cache buffer 50. For instance, the data cache 20 may drain the cache line having the dirty state to the speculative cache buffer 50 because a speculative store has to be performed to the cache line in the data cache 20. If the cache line having the speculative state is later drained to the speculative cache buffer 50 and if a commit operation is performed, then the speculative cache buffer 50 would have two cache lines with different versions of the data, whereas only one version of the data needs to be drained to a memory component such as L2 data cache, main memory, etc.
[0036] In an alternate embodiment of the speculative cache buffer 50, the plurality of states also includes a commit-kill state, in addition to the invalid state, the dirty state, and the speculative state. The commit-kill state indicates that the data cache 20 has evicted the respective cache line having the dirty state in response to a speculative modification operation (or speculative store) to the respective cache line in the data cache 20. The commit-kill state reduces the number of copies of a cache line in the dirty state and saves bandwidth in case of the commit operation, as detailed below.
[0037] FIG. 5 illustrates a second state diagram of a speculative cache buffer in accordance with a second embodiment. As described above, a cache line can have an invalid state I, a dirty state D, a commit-kill state K, or a speculative state S.
[0038] Invalid State I
[0039] Assuming the cache line is in the invalid state I, there are several possibilities for this cache line. If the data cache 20 evicts a cache line having the dirty state D but not due to a speculative store operation, the cache line moves to the dirty state D. If the data cache 20 evicts a cache line having the speculative state S, the cache line moves to the speculative state S. If the data cache 20 evicts a cache line having the dirty state D in response to a speculative store operation to that cache line, the cache line moves to the commit-kill state K.
[0040] Dirty State D
[0041] Assuming the cache line is in the dirty state D, there are several possibilities for this cache line. If the speculative cache buffer 50 drains the cache line having the dirty state D to a memory component such as L2 data cache, main memory, etc., the cache line moves to the invalid state I. In case the data cache requests the cache line back, it moves to the invalid state I in the speculative cache buffer.
[0042] Speculative State S
[0043] Assuming the cache line is in the speculative state S, there are several possibilities for this cache line. If a commit operation is performed, the cache line moves to the dirty state D. If a rollback operation is performed, the cache line moves to the invalid state I. In case the data cache requests the cache line back, it moves to the invalid state I in the speculative cache buffer.
[0044] Commit-Kill State K
[0045] Assuming the cache line is in the commit-kill state K, there are several possibilities for this cache line. If a commit operation is performed, the cache line moves to the invalid state I. If a rollback operation is performed, the cache line moves to the dirty state D. If the speculative cache buffer 50 drains the cache line having the commit-kill state K to a memory component such as L2 data cache, main memory, etc., the cache line moves to the invalid state I.
[0046] The foregoing descriptions of specific embodiments have been presented for purposes of illustration and description. They are not intended to be exhaustive or to limit the disclosure to the precise forms disclosed, and many modifications and variations are possible in light of the above teaching. The embodiments were chosen and described in order to best explain the principles of the disclosure and its practical application, to thereby enable others skilled in the art to best utilize the disclosure and various embodiments with various modifications as are suited to the particular use contemplated. It is intended that the scope of the disclosure be defined by the Claims appended hereto and their equivalents.
User Contributions:
Comment about this patent or add new information about this topic: