Patent application title: DETECTION OF PHISHING ATTEMPTS
Inventors:
Amit Klein (Herzliya, IL)
Amit Klein (Herzliya, IL)
Michael Boodaei (Givatayim, IL)
Michael Boodaei (Givatayim, IL)
IPC8 Class: AH04L2906FI
USPC Class:
726 23
Class name: Information security monitoring or scanning of software or data including attack prevention intrusion detection
Publication date: 2015-12-17
Patent application number: 20150365433
Abstract:
A method for alerting a service provider and/or a user of a web browser
of a phishing attempt comprises providing on a page that it is desired to
protect against phishing, a Javascript that when caused by a phishing
page to run not in the context of the original page generates an
indication that a phishing attempt may exist.Claims:
1. A method for blocking illegitimate access to a computer-hosted
website, the method comprising: storing a web page on a computer-hosted
website, wherein the web page is configured to cause a web browser to a)
retrieve computer-executable instructions from the website when the web
page is rendered by the web browser, and b) execute the
computer-executable instructions to b1) determine a source address of the
web page, b2) determine whether the source address is associated with the
website, and b3) report to a computer server associated with the
computer-hosted website when the source address is not associated with
the website; and at least partly blocking access to the website
responsive to receiving the report at the computer server.
2. The method according to claim 1 and further comprising: configuring the computer-executable instructions to recover user credentials input into the web page and send the user credentials to a computer server associated with the website; and at least partly blocking access to the website in a manner that is associated with the user credentials.
3. A system for blocking illegitimate access to a computer-hosted website, the system comprising: a web page stored on a non-transitory, computer-readable storage medium of a computer-hosted website, wherein the web page is configured to cause a web browser to a) retrieve computer-executable instructions from the website when the web page is rendered by the web browser, and b) execute the computer-executable instructions to b1) determine a source address of the web page, b2) determine whether the source address is associated with the website, and b3) report to a computer server associated with the computer-hosted website when the source address is not associated with the website; and a computer server associated with the computer-hosted website, wherein the computer server is configured to at least partly block access to the website responsive to receiving the report.
4. The system according to claim 1 wherein the computer-executable instructions are configured to recover user credentials input into the web page and send the user credentials to a computer server associated with the website, and wherein the computer server is configured to at least partly block access to the website in a manner that is associated with the user credentials.
Description:
CROSS-REFERENCE TO RELATED APPLICATIONS
[0001] This application is a continuation of U.S. patent application Ser. No. 13/437,122 filed Apr. 2, 2012.
FIELD OF THE INVENTION
[0002] The present invention relates to the field of Internet security. More particularly, the invention relates to a method for preventing phishing attempts.
BACKGROUND
[0003] Phishing is defined as a way of attempting to acquire information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. One particularly dangerous type of phishing directs users to enter details at a fake website, e.g. the website of a financial institution, or a page which requires entering financial information, the look and feel of which are almost identical to the legitimate one. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.
[0004] Because of the ever-growing methods and attempts to obtain fraudulently this type of information there is a constant need to provide solutions that will alert users and service providers when a phishing attempt is suspected. It is an object of the present invention to provide a method and related means to achieve this goal.
SUMMARY
[0005] The invention is directed to a method for alerting a service provider and/or a user of a web browser of a phishing attempt, comprising providing on a page that it is desired to protect against phishing, a Java script® that when caused by a phishing page to run not in the context of the original page generates an indication that a phishing attempt may exist.
[0006] In one embodiment of the invention the indication that a phishing attempt may exist includes transferring data to the owner of the protected page. In another embodiment of the invention the indication that a phishing attempt may exist includes alerting the user, who has reached the phishing website.
[0007] Alerting can be effected through any suitable channel, such as via SMS, e-mail, etc., and according to one embodiment of the invention alerting is done through the user's browser.
[0008] The invention is also directed to a protected webpage comprising a Javascript® that when caused by a phishing page to run not in the context of the original page, generates an indication that a phishing attempt may exist.
BRIEF DESCRIPTION OF THE DRAWINGS
[0009] In the drawings:
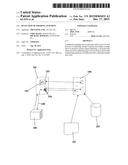
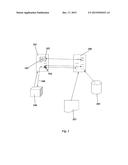
[0010] FIG. 1 schematically illustrates the operation of one illustrative embodiment of the invention.
DETAILED DESCRIPTION
[0011] Phishing websites masquerade as legitimate ones by presenting to the user a page that has the look and feel of the original page to which the user wanted to navigate (e.g., the log in page of his bank account). In many cases, however, the phishing website does not copy into the fake page JavaScript resources (".JS" files) and even images that are located on the page it is copying. Instead, when the user's browser reaches the phishing webpage, the JSs and the images are rendered from the original, legitimate website.
[0012] In a different scenario, fraudsters may copy the JS (with the additional code) to their own site (if they create their kit after the code according to the invention is deployed to the bank's site). In such a case, the method of the invention is still operative, although the JS code is used in the phishing site.
[0013] According to the invention phishing attempts of this type are discovered through the use of an added JS code (referred to hereinafter as "added JS code"), which is included with those JS resources that are not copied to the phishing website. When the phishing website invokes JS from the legitimate site, the added JS code checks the context of the website in which it is running and, if it is not running in the context of the legitimate website it determines that a phishing attempt is ongoing. This determination is carried out, for instance, by utilizing the "document.location" DOM property, which contains the current page's URL. When a phishing attempt is discovered in this way the added JS code can immediately report to the owner of the legitimate websites and/or to the user, and potentially block further access to the legitimate websites and/or alerting the user so he discontinues the submission of information to the phishing website.
[0014] The additional JS code can be programmed to perform additional activities on the phishing website. For instance, adding an on Submit event handler so that when the user submits credentials (in the phishing site), the added JS code recovers the credentials and sends them to an external server, thus enabling the genuine site owner (e.g., a bank) to freeze the user's account pending resolution of the issue.
[0015] Looking now at FIG. 1, a website 100, which may be a financial institute such as a bank, or any other service supplier, presents to its users a log-in page 101, which in this simplified example references a JS file 102, designed to run a conventional task (which is irrelevant to the invention and therefore not discussed in detail), and a New JS 103, which is found inside the original JS 102, as well as an image 104. A phishing website 105 generates a phishing (fake) Web page 106, which is designed to mislead a user, operating a browser 107, into believing that he has reached Web log in page 101, while in fact he has reached phishing page 106.
[0016] The phishing websites has not copied JS 102, and image 104 into web page 106, and when presenting it to browser 107 it renders them from original website 100. At this point New JS 103, which is part of JS 102 is run, identifies that it is running in the context of a page different from the original one and that, therefore, the alterations should be identified as a phishing attempt. In the simplified example of FIG. 1 New JS 103 alerts website 100 of the phishing attempt (arrow 108), which in turn takes corrective action according to its program, e.g., blocks the access of the user to the system and/or alerts him of the situation.
[0017] A special case, which is of particular interest, is when a Cascading Style Sheets is used. Cascading Style Sheets (CSS) is a style sheet language used to describe the presentation semantics (the look and formatting) of a document written in a markup language. Its most common application is to style web pages written in HTML and XHTML, but the language can also be applied to any kind of XML document, including plain XML, SVG and XUL. CSS is designed primarily to enable the separation of document content (written in HTML or a similar markup language) from document presentation, including elements such as the layout, colors, and fonts, to improve content accessibility and to provide more flexibility and control in the specification of presentation characteristics. The Internet Explorer browser allows running Javascript® inside CSS, via the "expression" property (see http://msdn.microsoft.com/en-us/library/ms537634%28v=vs.85%29.aspx). Thus, even if a phishing site does not embed any JS from the original site (but does embed at least one CSS file), it is still possible to employ the above technique by using the CSS expression with the added JS code in it (this works only for browsers which support the expression property in CSS).
[0018] All the above description has been provided for the purpose of illustration and is not intended to limit the invention in any way. Many different setups can be devised, in which different JSs are used to generate phishing notifications.
[0019] Moreover, the skilled person will easily devise many different arrangements for acting upon the discovery of a potential phishing attempt, all without exceeding the scope of the invention.
User Contributions:
Comment about this patent or add new information about this topic: